Week 3 - Putting a SOC in it
Improving my security posture and visibilty with Proxmox shenanigans on the side
Week 3 already? Just another entry to post.
This week
I went a bit ham this week and purchased a handful of hardware to load Proxmox onto. This proved a bigger headache than I initially planned… I decided that it was time to give the Proxmox nodes proper names (with me adding more to the cluster) so I renamed the cluster nodes following the Proxmox documentation. This… well… didn’t go as planned and turned more into a disaster recovery environment for about 30 minutes. I exported all the important files I needed from the containers to an external drive that I could later reference.
This proved helpful though, with everything exported off, I determined a fresh install was probably in order. So, I nuked the entire Proxmox environment and started from fresh. Now with better IP management, better VM/Container design and a fresh area to deploy into. Once cleared, I established a cluster and now can nicely access all the machines from a single machine’s interface.
You may wonder about the title… A SOC? Okay, maybe not exactly a complete security centre but I deployed a Wazuh stack. It’s a SIEM and XDR platform. It is open-source and free (unless you’re using their cloud service in which of course it’ll cost something, it’s a SaaS model after all). Having a SIEM was something I meant to set up for a long time. I investigated into Splunk but Splunk’s free tier is really bad for anything apart from basic learning and luckily, most SIEMs have the same style of design, therefore Wazuh seemed right.
It took two tries to get working, mainly having the indexer talk to the server and the server host out to the dashboard. Wazuh is scalable but deploying it as a single node stack is also very popular.
Yikes!
Yeah, I established Wazuh, hardened the system and established agents and oh boy… I believed my security awareness was pretty good. I always did updates when I saw them available to me, I always ran checksums to ensure I get the correct file at the end and I always made sure I’m not running anything dodgy on my system. However… When the initial report returned from my desktop agent. I was horrified to see:

WHAT?! 61 Critical vulnerabilities, 809 High vulnerabilities and over 100 Medium/Low vulnerabilities on my own machine? What is actually going on? Turns out, there is so much software on my computer that I may, at one point, have had one specific niche use case for that I hadn’t opened it in maybe 3-4 years. So, straight to remediation I went. I must’ve regained about 100GB of space by getting rid of software I just didn’t need. Did all that pay off? Well, this is what we got when the agent sent a report back:
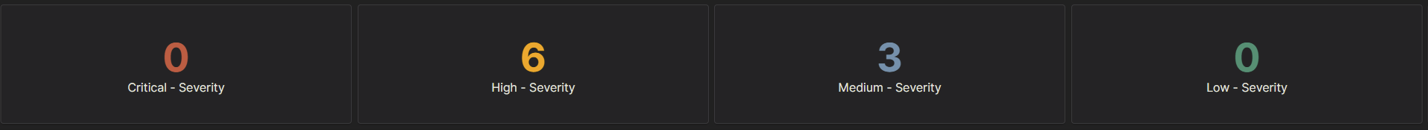
Much better and I found dark mode too. Light mode burns the retinas off you, so I’m glad I checked around for that setting. We can see that it doesn’t say 0 across the board, that’s because I have a few false positives and I’ve already cleared them and ensured that they are false before adding them to my ignore list.
Lessons learnt
Always plan like you are going to scale, even if you don’t and honestly just get rid of software you don’t use anymore. If you need to use it again, you can reinstall it again. It’s good to see that my attack surface has decreased massively. Till next week.